Getting the Azure Monitor Agent, formerly the Microsoft Monitor Agent (MMA) and Operations Management Suite (OMS) agent, installed on servers, and more importantly installed on new servers is not a very fun or enjoyable task. There are a number of ways to do it. In this post I’ll show you how to do it, and in my opinion, the easiest and most efficient way, using Azure Policy.
First I’ll show a few of the different ways to install the agent.
ARM Template
Hopefully this is not the first time you’re reading about an ARM template. If it is, in Azure you can do deployments as code using JSON. So you can attach this to your existing ARM template deployments to deploy the Azure Monitor agent. https://docs.microsoft.com/en-us/azure/virtual-machines/extensions/oms-windows
{
"type":"extensions",
"name": "OMSExtension",
"apiVersion": "[variables(‘apiVersion’)]",
"location": "[resourceGroup().location]",
"dependsOn": [
"[concat(‘Microsoft.Compute/virtualMachines/’, variables(‘vmName’))]"
],
"properties": {
"publisher": "Microsoft.EnterpriseCloud.Monitoring",
"type": "MicrosoftMonitoringAgent",
"typeHandlerVersion":"1.0",
"autoUpgradeMinorVersion": true,
"settings": {
"workspaceId": "myWorkSpaceId"
},
"protectedSettings": {
"workspaceKey": "myWorkspaceKey"
}
}
}
This is definitely a good way to do it, but also depends on everyone using the same ARM template(s) for deployments. There is also no audit of it being done on new deployments.
Workspace Data Sources
Next, under the Log Analytics workspace, under Workspace Data Sources you have Virtual Machines, if you have machines here you could click on them and click connect and Azure will auto install the agent for you.
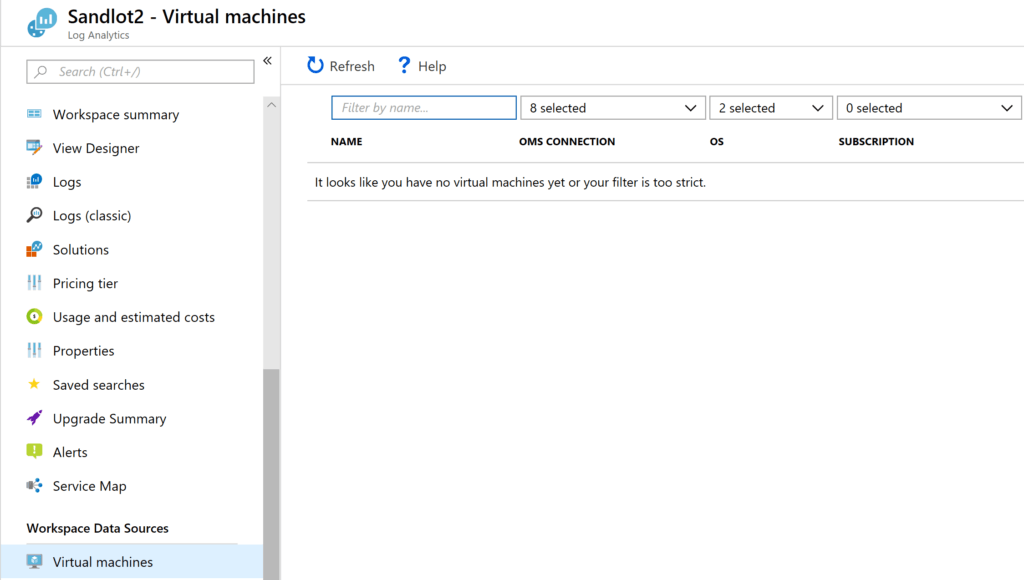
this is good for a one of senario, not bulk machine deployments.
Install Azure Monitor Agent with Azure Policy
Within Azure, there is a cool little service, Azure Policy. In Azure Policy there are a number of predefined Policies and Initiatives that you can assign, subscription wide or even down to select Resource Groups.
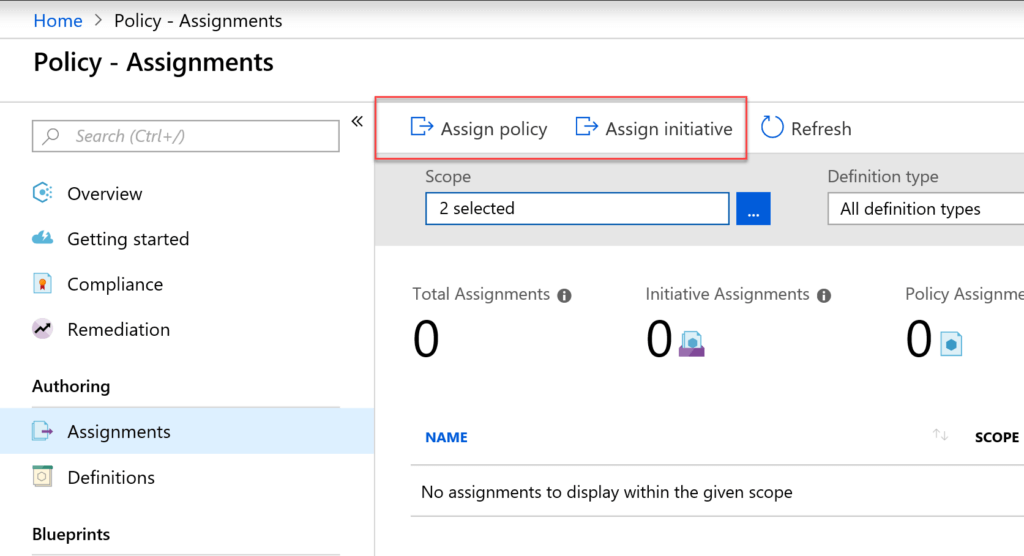
Taking a look at Assign Policy, there are two for deploying the Agent for Linux and Windows.
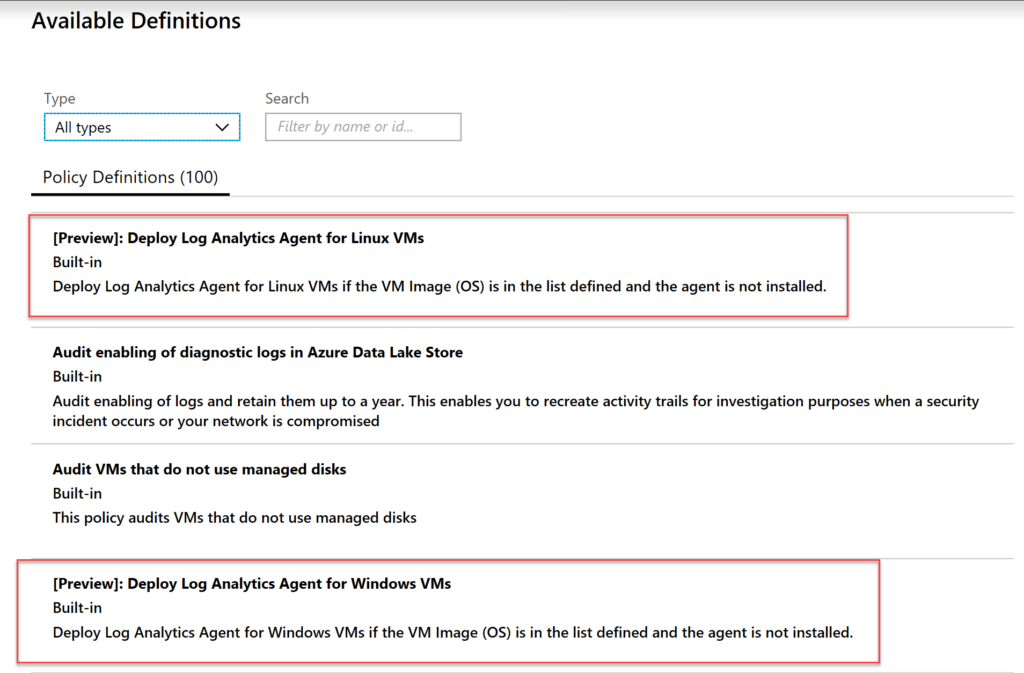
Assigning one of them gives us one policy assigned.
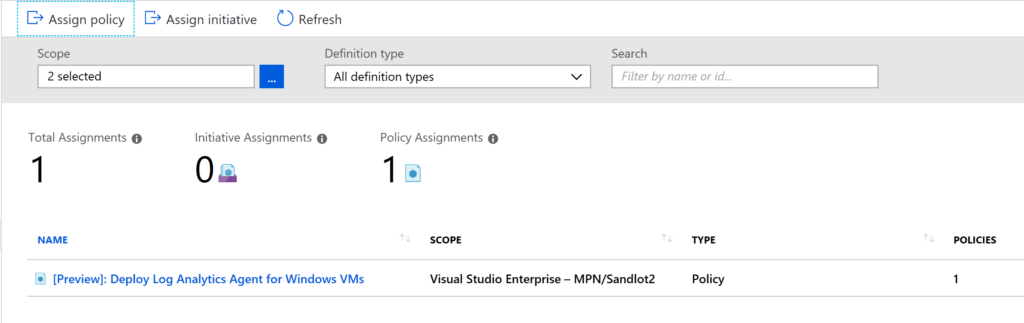
But what about Initiatives? Initiatives are multiple policies all rolled under one Initiative. Looking under Definitions there is “Enable Azure Monitor for VMs”
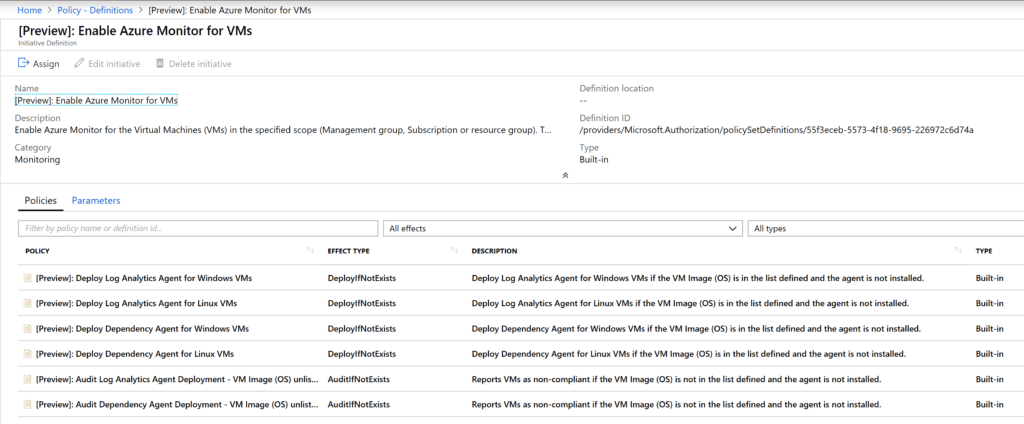
As you can see, there are multiple policies here. Not only for installing the agent on Linux and Windows, but auditing as well.
There is also an Initiative that enables Monitoring in Azure Security Center. Azure Security Center is closely connected with Azure Monitor, specifically logging to Log Analytics workspaces. These two Initiatives combine for 56 policies for installation of the Azure Monitor agent, and auditing your VMs. I would highly recommend taking a look at both initiatives for your environment.
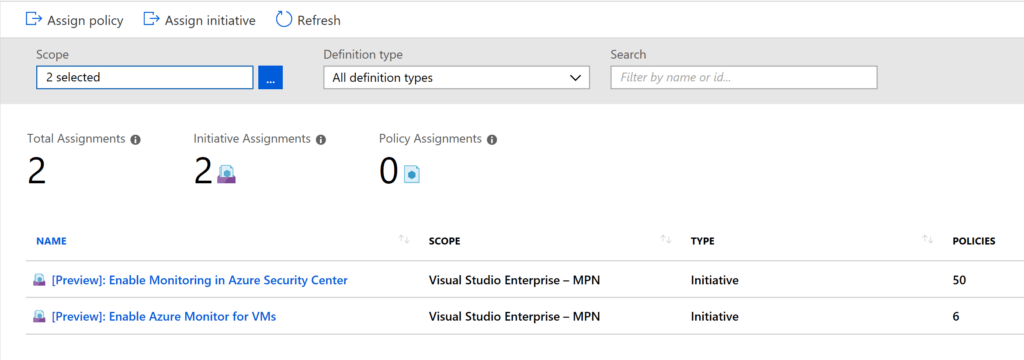
You can learn more about Azure Policy here. https://docs.microsoft.com/en-us/azure/governance/policy/overview
This post obviously covers installation of the the Agent in Azure. For on-prem I would recommend using SCCM or Powershell DSC for installation and auditing.